Securing APIs with the Okta Dance!
Dec 22, 2023Have you ever taken dancing lessons to learn to dance? It is very awkward, and if you get the steps wrong, it can be quite embarrassing. If your APIs are not properly secured, it can be more than embarrassing, it can be catastrophic.
One of the ways to secure your APIs on Anypoint Platform is by configuring an OpenID Connect Dynamic Client (OIDC) provider. This blog will cover the first step of three to secure your APIs. We affectionally call the authentication process the “Okta Dance”. So, I ask, “Won’t you Dance with me? Let’s learn the Okta Dance!” Ready? 1, 2, 3, 4….

Okta Dance Steps!
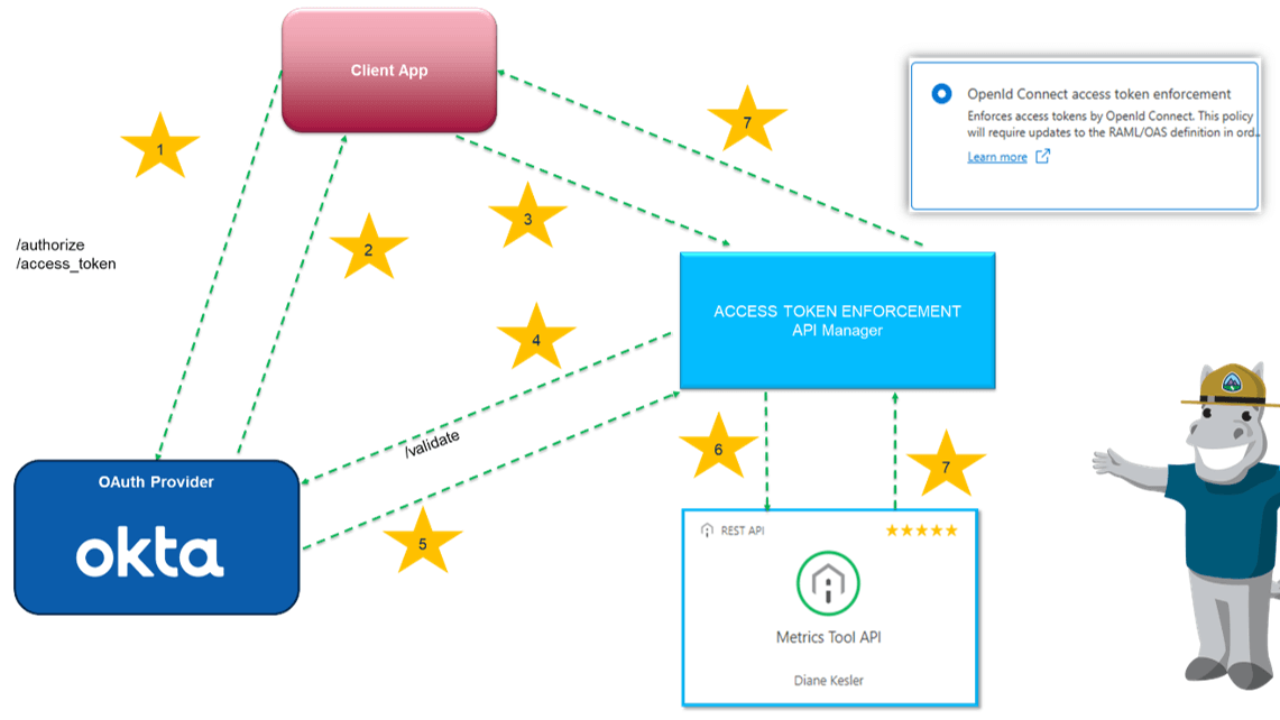
- The client requests an access token via Okta server.
- A Bearer access token is returned to the Client.
- A request is sent to Secured API.
- API Manager OIDC Policy validates the access token against Okta server.
- Validation is approved.
- Request proceeds to the API.
- Response is returned to the Client.
Seems easy enough! As with any dance party, planning and setup are required before the big day! We begin by setting up an Okta Developer Account, Authorization Server, and a Web Application on developer.OKTA.com.
Getting Started: Create a notes document
Start an Okta notes document. Be sure to carefully secure this document with encryption. You will add important information to save and use for testing and configuration throughout this series. In your notes, add the following:
Okta Developer:
- Account Username:
- Account Password:
- Your Okta URL:
Authorization Server Metadata:
- "Issuer":
- "authorization_endpoint"
- "token_endpoint"
- "registration_endpoint"
- "jwks_uri"
Token:
- Token Name
- Token Value
- Token ID
Web Application:
- Client ID
- Client Secret
Setup Okta Developer Account
- Navigate to https://developer.okta.com/signup/ to create an account.
- Select the Developer Edition.
- Follow the process to sign up, activate your account, set your password, and add to your Okta notes document.


Authorization Server
Okta creates an authorization server by default. For this tutorial, use the default one.
- Click Security > API

2. Click the Edit Icon

3. Click the Metadata URL, and a browser tab will open with all of the URLs associated with your Authentication Server.
4. Save the URLs to your secured notes document.

Create a Token
- Return to the server page, select Security>API
- Click the Tokens tab, click Create token

3. Name the token (something meaningful) and Click Create token
a. okta-token-{unique identifier}

4. Token value is created; add the token name and value to your OKTA Notes document.

5. Once returned to the token summary page, copy the Token ID to your Otka Notes document.

Create Web Application
- From the left panel menu, select Applications > Applications
- Click Create App Integration

3. Select OIDC – OpenID Connect and click Web Application

4. Add Name (Ex: Token Introspection Client)
5. Grant Type: select Client Credentials
6. Assignments: select Skip group assignments for now, and Save

7. New Application is displayed, copy the Client ID and Client Secret to your OKTA Notes document

Create Scope
- Return to the Authorization Server page, click Security>API
- Click Edit icon

3. Click the Scopes tab, click Add Scope

4. Configure Scope
a. Add Name (ex: mule-okta-scope
b. Add Display Name: (ex: mule-okta-scope
c. Add Description: MuleSoft Scope
d. Create
Time to TEST your MOVES!
We have completed the configuration needed on Okta.com, now we are ready to put our work to the test! Get up on stage and practice the first steps of the Okta Dance!!
- Change the method to POST and add the URL of the “token_endpoint” from your metadata
- Add Headers:
a. Header name: content-type
b. Header value: application/x-www-form-urlencoded

3. Add Authorization: Bearer
a. Choose Bearer and slide the toggle to the right.
b. Token: SSWS {add token value}

4. Query Parameters
a. Name: grant_type
b. Value: client_credentials
c. Name: scope
d. Value: {the name of your scope}
5. Send in Request, Authentication required
a. Username: {Enter Web Application Client ID}
b. Password: {Enter Web Application Client Secret}

c. Response with access_token is returned!

Watch Diane explain the Okta Dance on the MuleSoft Community Stream!!!!
Congratulations! You have completed the first Okta Dance Challenge! Challenge 2 is for us to configure the Client Provider on Anypoint Platform. Keep those dance shoes on, we are about to bust some moves!
Don't miss a beat!
Join our email list for platform updates and new resources.
We hate SPAM. We will never sell your information, for any reason.

